The cybersecurity landscape in 2025 continues to evolve at an unprecedented pace. With new vulnerabilities emerging daily, organizations across industries are investing heavily in professionals who can understand, anticipate, and combat digital threats. One of the most recognized certifications in this domain is the Certified Ethical Hacker (CEH) credential offered by EC-Council. But before diving into whether it’s worth pursuing, it’s essential to understand what CEH is and who it’s designed for.
This article sets the foundation for a four-part exploration of the CEH certification. Here, we’ll discuss the core purpose of CEH, what it covers, and which professionals will benefit most from it. If you’re considering a move into offensive cybersecurity or simply looking to strengthen your credibility, understanding the scope of this credential is a vital first step.
What is the CEH Certification?
The Certified Ethical Hacker certification is a professional credential that validates a candidate’s ability to identify weaknesses in computer systems and networks using the same tools and knowledge as malicious hackers, but with legal and ethical intent. Administered by the International Council of E-Commerce Consultants (EC-Council), the CEH program has gained global recognition since its inception.
CEH is often seen as a foundational certification for penetration testing and ethical hacking. It’s designed to prove that the holder understands how to assess network security, exploit vulnerabilities in a controlled environment, and recommend countermeasures to protect data and infrastructure.
The certification doesn’t just test theoretical knowledge. It emphasizes how to think like an attacker and apply that mindset to defend an organization. Topics covered in CEH include footprinting, scanning networks, enumeration, system hacking, malware threats, sniffing, denial of service, session hijacking, and evasion techniques.
In recent versions, the certification has expanded its reach into emerging domains such as cloud security, mobile security, IoT vulnerabilities, and operational technology threats. These additions make CEH more relevant in today’s cloud-driven and hybrid network environments.
Why CEH Matters in Cybersecurity Today
The demand for ethical hackers and cybersecurity specialists has never been higher. Data breaches, ransomware attacks, and cyber espionage are now daily threats to organizations of every size. Governments, healthcare providers, banks, and manufacturers all need security professionals who understand how attackers think and operate.
CEH-certified professionals are trained to assess risk by simulating real-world attacks. This proactive approach enables companies to find and fix vulnerabilities before malicious actors exploit them. As a result, CEH is often a baseline requirement for roles in penetration testing, red teaming, and security analysis.
Employers value CEH because it demonstrates that a candidate understands offensive security tools, techniques, and procedures (TTPs) in a structured and legally compliant manner. Furthermore, because the certification is vendor-neutral, it equips professionals with skills that can be applied across a wide range of platforms and environments.
Core Domains Covered by CEH
The CEH exam is based on nine primary domains, each of which represents an area of competence in ethical hacking and information security. These domains provide a broad understanding of how attackers compromise systems and how defenders can counter those techniques.
- Information Security and Ethical Hacking Overview
This section introduces hacking concepts, cyber threats, attack vectors, and ethical hacking methodologies. - Reconnaissance Techniques
Covers passive and active information gathering techniques used to identify potential entry points. - System Hacking Phases and Attack Techniques
Focuses on password cracking, privilege escalation, spyware, keyloggers, and rootkits. - Network and Perimeter Hacking
Includes sniffing, spoofing, session hijacking, denial of service attacks, and firewall evasion. - Web Application Hacking
Explores SQL injection, cross-site scripting (XSS), remote file inclusion (RFI), and other web vulnerabilities. - Wireless Network Hacking
Examines wireless encryption protocols, rogue access points, and wireless attacks. - Mobile, IoT, and OT Hacking
Addresses security concerns related to mobile devices, IoT deployments, and industrial control systems. - Cloud Computing
Discusses cloud-specific vulnerabilities, shared responsibility models, and virtualized environments. - Cryptography
Covers encryption, hashing, cryptographic attacks, and public key infrastructure (PKI).
This broad scope makes CEH a valuable certification for professionals working across the security spectrum, from penetration testers to IT administrators and architects.
Who Should Pursue the CEH Certification?
While the CEH is open to anyone, it’s most useful to individuals who work or plan to work in roles that involve identifying and mitigating security risks. Below are the professionals who benefit most from CEH certification in 2025.
Cybersecurity Analysts
Security analysts are often responsible for monitoring networks, investigating alerts, and assessing threats. CEH equips them with the skills to recognize early-stage attacks and understand how adversaries might exploit system vulnerabilities. This knowledge enables analysts to improve their organization’s threat detection capabilities and support incident response efforts.
Penetration Testers
Pen testers, or ethical hackers, simulate cyberattacks to test the strength of an organization’s defenses. CEH covers the core tools and techniques used during penetration testing engagements, including reconnaissance, exploitation, and post-exploitation phases. It serves as an entry point into the world of red teaming and ethical offensive security testing.
Security Engineers and Architects
Engineers and architects who design and maintain network infrastructure benefit from CEH by learning how attackers can bypass security controls. This insight allows them to build more secure systems, incorporate defense-in-depth strategies, and anticipate future attack vectors. CEH is particularly helpful for IT professionals transitioning from infrastructure into security roles.
Security Consultants
Consultants who advise organizations on cybersecurity strategies and policies can use CEH to enhance their credibility and demonstrate technical proficiency. Having a deep understanding of vulnerabilities and threat actor behavior allows consultants to provide actionable recommendations that go beyond theory and policy.
CISOs and Security Managers
Chief Information Security Officers (CISOs) and information security managers often oversee technical teams but may not be involved in hands-on security testing. However, earning a CEH can bridge the knowledge gap, making it easier to lead technical initiatives, evaluate risk assessments, and communicate effectively with both technical staff and non-technical stakeholders.
IT Professionals Transitioning into Security
System administrators, network engineers, and other IT professionals often find themselves drawn to cybersecurity due to its growth and opportunity. CEH provides a structured entry point into the field, offering exposure to tools and concepts that may be unfamiliar in traditional IT roles. For many, CEH serves as a launching pad for more advanced security certifications and roles.
Career Changers and Students
Individuals transitioning from unrelated fields or recent graduates pursuing cybersecurity as a new career can benefit from CEH by gaining a credential that is recognized and respected globally. While it’s not necessarily the first certification for absolute beginners, those with foundational IT knowledge can use CEH to quickly gain credibility and job-readiness.
CEH and Regulatory Compliance
Another compelling reason to pursue CEH is its alignment with compliance requirements. The certification is approved for six job roles under the U.S. Department of Defense Directive 8140/8570. This means that individuals seeking employment in federal cybersecurity positions, either as direct government employees or contractors, will often need CEH or an equivalent certification to qualify.
In industries with strong regulatory environments, such as healthcare or finance, CEH-certified professionals are increasingly being hired to meet audit and compliance needs. Demonstrating ethical hacking knowledge shows a proactive stance on risk mitigation, which regulators appreciate.
CEH in the Global Job Market
The CEH certification holds strong value in global hiring markets. Job listings across North America, Europe, Asia, and the Middle East frequently reference CEH as either a preferred or required qualification for cybersecurity roles. This global relevance makes CEH a smart choice for professionals looking to work in multinational environments or remotely for global companies.
With cybersecurity talent shortages continuing in many regions, employers are looking for professionals who can demonstrate competence quickly. Holding the CEH not only validates your knowledge but also shows initiative and dedication to staying current in a dynamic field.
CEH Certification Costs and Training Options – What You Need to Know in 2025
Pursuing the Certified Ethical Hacker (CEH) certification is a significant step for anyone looking to specialize in offensive cybersecurity. The CEH is well-respected globally and often appears in job descriptions for ethical hackers, penetration testers, and cybersecurity consultants. However, one of the biggest questions aspiring candidates face is how much it costs to get certified, and whether the investment is truly worth it.
In Part 1 of this series, we examined what the CEH certification is and who it is best suited for. Now, in Part 2, we’re diving into the costs associated with CEH certification, the various training options available, and how to make an informed decision about which path to choose. We’ll also explore how tools like Exam-Labs can significantly reduce your preparation expenses while helping you pass with confidence.
Understanding the True Cost of CEH Certification
The pricing of the CEH certification can be confusing at first glance. EC-Council offers multiple training tiers and exam packages, and your final cost will depend on how you choose to prepare. In 2025, the costs vary based on whether you pursue training through EC-Council or apply for the exam using verified experience.
Let’s break down the core elements that contribute to the overall CEH certification cost.
Application and Exam Fees
If you already have two years of verifiable experience in information security, you can bypass official EC-Council training by submitting an eligibility application. This route requires:
- Application fee: $100 (non-refundable)
- Exam voucher: $1,199 for Pearson VUE or $950 for the EC-Council exam center
- Remote proctoring fee: $100 (if taking the exam remotely)
Candidates who go this route will pay around $1,199 to $1,399 depending on where they take the exam.
Official EC-Council Training Packages
For those without prior experience or for candidates who prefer official training, EC-Council offers several options. Each includes different combinations of study materials, lab access, and exam vouchers.
1. Digital Courseware ($850 + $550 exam voucher)
This is the most affordable EC-Council training option. It includes basic study materials but requires you to purchase the exam voucher separately. Combined, it costs around $1,400, not including tax or remote proctoring.
2. On-Demand ($2,199)
The On-Demand package includes:
- Video-based training
- eCourseware
- Exam voucher
- 6 months of lab access
- CEH practice questions
- One retake
- CEH Practical and Challenge Labs
This bundle is ideal for self-paced learners who want structure but don’t need live instruction.
3. Unlimited On-Demand ($2,999)
This plan gives access to the entire EC-Council training library, including all current and future courses. It’s useful for professionals planning to earn multiple certifications.
4. Live Training ($3,499)
Includes everything in the On-Demand package plus live instructor-led sessions. The course can be taken in a classroom or remotely.
As you can see, the price of EC-Council training can climb quickly. Candidates who choose live or unlimited access options can expect to pay over $3,000 to $3,500, before taxes and optional add-ons.
Exam Retake Fees
If you don’t pass on your first attempt, retake vouchers are available at:
- $499 for Pearson VUE or EC-Council retake exams
Retakes are included in some EC-Council packages but must be purchased separately otherwise.
Summary of CEH Costs
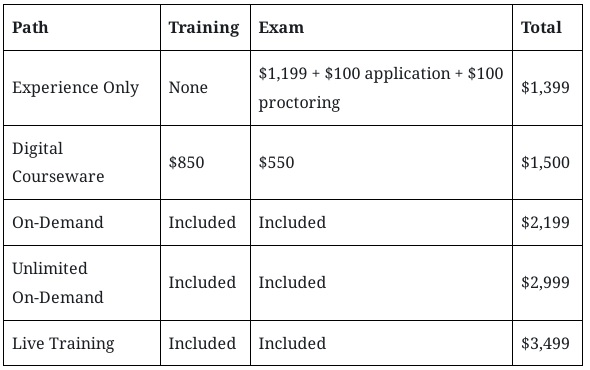
Prices are approximate and may vary with region or promotions.
Is EC-Council Training Necessary?
One of the most common questions is whether you must purchase EC-Council training to succeed. The short answer is no, as long as you have the experience, you can apply directly to sit for the exam and use third-party study materials.
However, EC-Council’s training is sometimes required for candidates who don’t have two years of security-related experience. In this case, an official course waives the need to submit experience documentation.
If you already work in IT, security, or a related field, you may qualify to skip official training and opt for independent preparation. This is where affordable and high-quality platforms like Exam-Labs can provide a major advantage.
Affordable Alternatives: Using Exam-Labs for CEH Preparation
Preparing for the CEH doesn’t have to involve spending thousands on training packages. With focused effort and the right tools, many candidates pass the exam by self-studying with trusted third-party resources.
Exam-Labs is one of the most popular platforms among certification candidates, offering:
- CEH practice tests that simulate the real exam format
- Scenario-based questions aligned with the CEH exam blueprint
- Detailed explanations for each answer
- Progress tracking and score analytics
- Real-world lab scenarios for ethical hacking
Using Exam-Labs alongside a CEH study guide and a home lab setup can significantly reduce your total certification cost. With a typical monthly subscription under $60, Exam-Labs gives you access to up-to-date, exam-relevant materials without locking you into expensive vendor programs.
This path is especially useful if you already understand cybersecurity basics or have hands-on experience. You can customize your study plan based on weak areas and use Exam-Labs’ quizzes and simulations to validate your knowledge.
Choosing the Right Path for You
The ideal CEH preparation path depends on your background, budget, and learning preferences. Below are a few common profiles and the recommended routes:
Beginner with No Experience
- Recommended Path: EC-Council On-Demand or Live package
- Cost: $2,199 – $3,499
- Why: Includes exam access, labs, retake option, and structured training
IT Professional with Security Experience
- Recommended Path: Self-study using Exam-Labs and CEH books
- Cost: $1,050 – $1,400
- Why: Leverage existing knowledge, use practice tests, and avoid high-cost training
Career Switcher with Budget Constraints
- Recommended Path: CEH exam via experience route + Exam-Labs + GitHub/YouTube content
- Cost: Under $1,500 total
- Why: Access free or low-cost content, simulate real exam conditions with Exam-Labs
Multi-Certification Seeker
- Recommended Path: Unlimited On-Demand package
- Cost: $2,999
- Why: Get long-term access to EC-Council’s full certification library
Avoiding Common Costly Mistakes
When investing in CEH certification, some candidates make avoidable financial missteps. Here are some tips to help you stay within budget:
- Don’t pay for EC-Council training if you already qualify via experience
- Don’t ignore retake policies, practice before scheduling the official exam
- Avoid outdated prep materials; always check the exam version
- Take advantage of Exam-Labs trial periods to assess value
- Use EC-Council’s CEH readiness quiz to assess preparedness before paying full exam fees
Being strategic with your preparation and resource selection can save you hundreds, if not thousands of dollars.
Promotions and Scholarships
EC-Council occasionally runs promotional discounts, especially during cybersecurity awareness month in October or at the end of the year. These can reduce training or bundle costs significantly.
Scholarships are also available through:
- EC-Council Hero Program (for veterans and first responders)
- Women in Cybersecurity programs
- University partnerships
- Employer reimbursement programs
Be sure to check eligibility criteria and apply early, as spots for scholarships and discounts are limited.
The Skills You Learn from CEH and How They Apply in the Real World
The Certified Ethical Hacker (CEH) certification by EC-Council is not just a badge to display on your resume, it’s a comprehensive training program that teaches professionals how to think like a hacker and defend like a security expert. But what does CEH actually teach? And more importantly, how do those skills transfer to real-world cybersecurity jobs?
In this third installment of our series, we break down the knowledge areas and technical abilities covered in CEH. We also look at how these competencies align with the day-to-day responsibilities of penetration testers, SOC analysts, cybersecurity consultants, and other roles. Whether you’re considering CEH as a way to validate your knowledge or as a stepping stone to a specialized role, understanding the skills you’ll gain is essential.
The CEH Curriculum: What You’ll Learn
CEH is structured to teach both theoretical knowledge and practical tools that security professionals use to identify, exploit, and patch vulnerabilities. EC-Council has mapped the CEH content across nine major domains, each reflecting a critical area in the offensive security landscape.
The domains focus on:
- Reconnaissance and intelligence gathering
- Scanning and enumeration techniques
- Gaining access through exploits
- Maintaining access and covering tracks
- Web, cloud, IoT, and wireless security testing
- Malware threats and evasion techniques
- Cryptographic attacks
- Social engineering
- Vulnerability analysis and assessment
Each of these areas contributes to a well-rounded understanding of how attackers operate, and how security teams can proactively defend systems and respond to breaches.
Let’s explore each category and connect it to real-world scenarios.
Reconnaissance: Gathering Target Information
CEH teaches passive and active reconnaissance methods, such as:
- DNS enumeration
- WHOIS lookups
- OSINT (open-source intelligence) techniques
- Google hacking
In a real-world job, a penetration tester uses these techniques to gather intelligence about a target organization before launching a simulated attack. The data collected in this phase helps identify public-facing assets, discover exposed email addresses, and locate weak points in a company’s digital presence.
SOC analysts and blue team members benefit from this knowledge by understanding how attackers collect pre-engagement intelligence, helping them better harden external systems and monitor early attack signals.
Scanning Networks and Enumerating Systems
In this domain, CEH focuses on:
- Port scanning with Nmap
- Vulnerability scanning using Nessus or OpenVAS
- Banner grabbing
- Identifying services and hosts on a network
This knowledge is used during internal or external assessments to understand a system’s attack surface. In a corporate environment, these tools help ethical hackers detect misconfigured services, outdated software, or weak authentication settings.
Security engineers use these skills to validate their firewall rules and ensure that unnecessary ports and services aren’t exposed to the internet.
Gaining Access: Exploiting Vulnerabilities
This is the heart of ethical hacking. CEH teaches how attackers exploit:
- Buffer overflows
- Weak passwords
- Unpatched systems
- Web application flaws
- Misconfigured cloud services
Students learn to use tools like Metasploit, Hydra, and Burp Suite to simulate these attacks in lab environments. In real-world penetration testing, this stage involves identifying critical weaknesses that could allow attackers to break into systems.
Cybersecurity consultants may use this skill set during vulnerability assessments, while security architects use the knowledge to build systems that resist these types of intrusions.
Maintaining Access and Covering Tracks
Advanced attackers often stay inside networks for weeks or months before detection. CEH covers:
- Rootkits
- Backdoors
- Persistence techniques
- Log tampering
- Steganography
Understanding how attackers maintain access enables blue teams to detect long-term compromises and implement better monitoring. Incident response teams also benefit from this training, as they learn what signs to look for during forensic analysis.
Web Application Attacks
CEH delves into common vulnerabilities listed in the OWASP Top 10, including:
- SQL injection
- Cross-site scripting (XSS)
- File inclusion
- Cross-site request forgery (CSRF)
- Web server misconfigurations
These vulnerabilities are among the most frequently exploited in real-world attacks. For example, an insecure input field on a public-facing website could allow an attacker to extract or modify sensitive database records.
Application security professionals, bug bounty hunters, and developers benefit from this knowledge by learning how to test and fix security issues in their web applications.
Wireless, IoT, and Mobile Security
With the increasing use of wireless networks, mobile devices, and IoT systems, CEH provides training in:
- Wireless encryption attacks (WEP/WPA2 cracking)
- Rogue access points
- Bluetooth exploitation
- Mobile OS vulnerabilities
- Smart device risks
These topics prepare professionals to assess the security of modern infrastructure beyond traditional data centers. In industries like healthcare, retail, and manufacturing—where IoT is prevalent—this knowledge is critical for reducing attack surfaces.
Security architects and red teams can simulate attacks on wireless networks and IoT devices, helping to identify configuration errors or weak device firmware.
Cloud and Virtualized Environment Security
As cloud adoption continues, CEH includes updated content on:
- Cloud service vulnerabilities
- Insecure API usage
- Misconfigured cloud storage
- Virtual machine escape attacks
Security professionals working with AWS, Azure, or Google Cloud learn how to test these environments using tools like ScoutSuite and Pacu. Real-world use cases include testing cloud storage permissions and identifying exposed access keys or insecure IAM roles.
Cloud security engineers and DevSecOps teams rely on this information to secure hybrid and multi-cloud deployments.
Cryptography and Encryption Attacks
CEH covers the foundations of cryptographic security, including:
- Symmetric and asymmetric encryption
- Hashing algorithms
- Digital signatures
- Man-in-the-middle (MITM) attacks
- Certificate spoofing
Understanding how encryption works, and how it can be bypassed, is essential for anyone implementing secure communication protocols or managing encrypted data storage.
Information security managers and compliance officers can use this knowledge to evaluate the strength of encryption across the organization and ensure regulatory standards are being met.
Vulnerability Assessment and Risk Analysis
Before launching an attack, ethical hackers must assess system weaknesses. CEH teaches how to:
- Conduct vulnerability assessments
- Interpret scan results
- Prioritize risks based on severity and impact
- Recommend remediation strategies
These are essential tasks for vulnerability management programs. Security teams need to conduct regular scans, report findings, and work with stakeholders to implement fixes. CEH graduates are well-equipped to carry out these responsibilities.
Applying CEH Skills On the Job
The knowledge gained from CEH is not theoretical—it’s practical and immediately applicable in many roles. Below are examples of how professionals across cybersecurity disciplines use CEH in their daily work.
Security Analysts
- Monitor systems for abnormal behavior using insights from reconnaissance and exploitation techniques
- Identify indicators of compromise linked to persistence mechanisms taught in CEH
- Evaluate network logs with better context about common attack vectors
Penetration Testers
- Design and execute full-scale red team assessments using the CEH framework
- Perform web app, wireless, and cloud penetration tests using CEH tools and methodology
- Generate detailed reports with attack paths and mitigation suggestions
Security Engineers
- Harden systems against the attack strategies learned in CEH
- Build better firewalls and intrusion detection systems by understanding evasion techniques
- Collaborate with SOC teams to respond to simulated incidents
Security Consultants
- Deliver professional vulnerability assessments using the CEH process
- Communicate technical risks in language that clients and executives understand
- Implement remediation projects based on CEH findings
Managers and CISOs
- Gain technical insight to lead security projects more effectively
- Understand the risk landscape and prioritize resources accordingly
- Coordinate incident response efforts based on real attacker TTPs
Reinforcing Skills Through Practice
The CEH exam is multiple-choice, but mastering the skills it teaches requires hands-on practice. Setting up a home lab using virtual machines and intentionally vulnerable systems like Metasploitable or DVWA (Damn Vulnerable Web App) can solidify concepts.
To supplement this, platforms like Exam-Labs provide:
- Realistic CEH exam simulations
- Interactive quizzes based on actual exam objectives
- Explanations for why each answer is correct or incorrect
- Progress tracking and domain-specific practice
Using Exam-Labs helps bridge the gap between theoretical study and practical application, ensuring that you’re not just memorizing facts but actually learning how to use the tools and techniques.
The Career Value and Long-Term ROI of CEH Certification
In the ever-evolving cybersecurity landscape, certifications have become a key benchmark for demonstrating knowledge, verifying skills, and advancing professionally. Among these, the Certified Ethical Hacker (CEH) credential has earned global recognition as one of the leading ethical hacking certifications. But is it worth the time, effort, and cost?
In the previous three parts of this series, we covered what the CEH certification entails, the costs involved, and the practical skills you gain. In this final segment, we will evaluate the career impact of the CEH, including its value in the job market, salary potential, recognition by employers, and how it compares to other cybersecurity credentials in terms of long-term return on investment.
CEH and the Cybersecurity Job Market
With cyber threats becoming more sophisticated, the demand for professionals who can think like attackers has skyrocketed. Organizations need experts who can identify and exploit vulnerabilities in a controlled manner to help defend networks and systems from real-world threats. This is where CEH-certified professionals come in.
The CEH credential is commonly listed as a preferred or required qualification in job descriptions for roles such as:
- Ethical Hacker
- Penetration Tester
- Information Security Analyst
- Network Security Engineer
- Red Team Operator
- SOC Analyst
- Cybersecurity Consultant
- Threat Intelligence Analyst
Because the CEH focuses on offensive security techniques, it is especially valuable for roles in penetration testing and red teaming. However, its coverage of system vulnerabilities, malware tactics, and reconnaissance techniques also benefits defensive security roles, such as blue team analysts and incident responders.
Government and DoD Recognition
A major factor contributing to CEH’s continued relevance is its inclusion in the U.S. Department of Defense Directive 8570/8140. This directive governs which certifications are approved for personnel working in federal cybersecurity roles.
CEH satisfies requirements for several DoD job categories, which makes it a gateway certification for cybersecurity professionals aiming to work with government agencies, contractors, or defense-related sectors. This recognition greatly enhances its credibility, particularly in North America, and has led to its adoption in many compliance-focused industries.
Salary Expectations for CEH-Certified Professionals
One of the most tangible measures of a certification’s value is the salary it can help command. CEH-certified professionals are among the better-paid individuals in cybersecurity, especially when paired with real-world experience or additional certifications.
According to industry sources and salary research from platforms such as Salary.com and Payscale, here are some average salary ranges in 2025 for job roles associated with CEH:
- Ethical Hacker: $95,000 – $130,000
- Penetration Tester: $90,000 – $120,000
- Information Security Analyst: $85,000 – $115,000
- Cybersecurity Consultant: $100,000 – $135,000
- Network Security Engineer: $95,000 – $125,000
- Security Operations Center (SOC) Analyst: $75,000 – $100,000
These figures can vary based on location, company size, years of experience, and whether you hold additional credentials. For example, a CEH-certified professional who also holds a CISSP, CySA+, or OSCP often commands higher salaries due to their combined skill sets.
It’s worth noting that many CEH-certified individuals report promotions or salary increases after earning the certification, as it signals a deeper understanding of offensive security tactics and improves technical credibility.
CEH and Career Advancement
Beyond salary, the CEH certification opens doors to advancement in various ways. For early-career professionals, it adds immediate credibility to a resume, demonstrating initiative and specialization in ethical hacking.
For mid-career professionals, CEH can facilitate a move from generalist roles like system administration into security-focused positions. It can also serve as a springboard to specialized roles, such as red team operator or vulnerability researcher.
For experienced cybersecurity professionals, CEH strengthens leadership potential. Security managers, architects, and even CISOs benefit from understanding offensive methodologies, allowing them to manage teams more effectively, evaluate risks with greater insight, and participate in strategic planning around cybersecurity initiatives.
Real-World Value in Interviews
The CEH credential often functions as a conversation starter in interviews. Employers know that CEH requires candidates to demonstrate a working knowledge of real attack techniques and tools. Having CEH on your resume indicates that you’ve been exposed to subjects such as reconnaissance, system exploitation, malware delivery, social engineering, and cryptographic attacks.
In many interviews, CEH-certified candidates are asked to elaborate on how they’ve applied these techniques in labs or professional settings. Those who have also prepared with hands-on resources like Exam-Labs can confidently describe attack simulations, penetration testing workflows, and remediation strategies—leaving a strong impression on hiring managers.
CEH Compared to Other Cybersecurity Certifications
To understand the full value of CEH, it’s helpful to compare it with other prominent certifications in ethical hacking and cybersecurity.
CEH vs. CompTIA PenTest+
PenTest+ is a newer certification that also targets penetration testers. It covers similar topics but leans more toward planning, scoping, and report writing rather than technical depth. CEH, on the other hand, goes further into specific tools and offensive techniques, making it more robust for hands-on professionals. PenTest+ is more affordable, but CEH carries greater recognition and industry weight, especially internationally.
CEH vs. Offensive Security Certified Professional (OSCP)
The OSCP is a more advanced and rigorous certification focused on practical penetration testing. Candidates must complete real-time hacking exercises during a 24-hour exam. While OSCP is more respected among senior red teamers, it is significantly more difficult and time-consuming than CEH. For professionals entering the field or looking for broad foundational knowledge, CEH is the more accessible first step.
CEH vs. CompTIA Security+
Security+ is often the first cybersecurity certification for IT professionals. It covers general security principles, risk management, and basic threat detection but doesn’t go deep into hacking tools or techniques. CEH offers a more technical and offensive perspective, which complements Security+ rather than replaces it.
CEH vs. CISSP
CISSP is a management-level certification focused on security architecture, governance, and leadership. While CEH is more technical and hands-on, CISSP appeals to professionals pursuing senior or executive roles. Many professionals pursue both, using CEH for technical credibility and CISSP for strategic positioning.
Long-Term ROI of CEH Certification
The long-term return on investment (ROI) of CEH goes beyond salary. Here are some of the other benefits that make it worth considering:
- Credibility in job applications: CEH often helps candidates stand out in competitive hiring pools.
- Opportunities for advancement: Many CEH holders report promotions into senior roles or team lead positions.
- Compliance and eligibility: For government, defense, or contract work, CEH satisfies critical certification requirements.
- Cross-functional respect: The knowledge gained through CEH helps professionals communicate more effectively across technical and leadership teams.
- Gateway to further learning: CEH provides a strong base for pursuing advanced certifications like OSCP, CPENT, or even GSEC.
When you factor in the average salary increase, career mobility, and real-world applicability, CEH offers a compelling long-term ROI—especially for professionals committed to offensive or hybrid security roles.
Maximizing CEH’s Value with Smart Preparation
Given CEH’s cost, preparation strategy plays a key role in maximizing its value. Candidates who invest wisely in study materials, practice exams, and hands-on labs often get more out of the certification than those who rely solely on memorization or expensive official courses.
Platforms like Exam-Labs help candidates prepare effectively by offering:
- CEH practice exams aligned with the latest version
- Scenario-based questions simulating real-world attacks
- Performance tracking to measure readiness
- Cost-effective alternatives to premium EC-Council training
Using Exam-Labs in conjunction with free labs (like TryHackMe or Hack The Box), CEH study guides, and open-source tools enables candidates to build deep, practical skills without breaking the bank.
Final Verdict: Is CEH Worth It?
The Certified Ethical Hacker certification continues to be a smart investment for cybersecurity professionals in 2025. Its blend of hands-on technical knowledge, industry recognition, and global relevance makes it a valuable credential for those entering the field or leveling up into more specialized roles.
While the cost may seem high at first glance, the long-term benefits: higher salary potential, improved job prospects, increased professional credibility, and eligibility for DoD roles – make it worth considering for most aspiring ethical hackers.
As with any certification, CEH is not a guarantee of success on its own. But when paired with experience, continuous learning, and effective preparation using resources like Exam-Labs, it becomes a powerful career accelerator.
