In today’s hyperconnected world, cybersecurity is not a luxury, it’s a necessity. As businesses move towards cloud-native environments, remote work, and digital expansion, traditional firewalls simply can’t keep up with the evolving threat landscape. That’s where next-generation firewalls (NGFWs) come into play. Designed to go beyond stateful inspection, NGFWs offer deep packet inspection, intrusion prevention, and application awareness. Among the leaders in this space are Palo Alto Networks and Fortinet. Each has carved out a significant presence in the cybersecurity market, offering robust NGFW solutions that cater to both enterprises and mid-size organizations.
What Defines a Next-Generation Firewall?
A next-generation firewall integrates several security features into a single platform. These typically include:
- Application-level inspection
- Intrusion prevention system (IPS)
- Identity-based access control
- URL filtering and DNS security
- Threat intelligence integration
- Centralized management
These capabilities help NGFWs not only inspect traffic based on port or protocol but also understand the content, context, and behavior of that traffic. It’s this intelligent processing that makes NGFWs effective against advanced persistent threats and zero-day attacks.
Palo Alto Networks: A Pioneer in NGFW Innovation
Palo Alto Networks is often recognized for setting a high standard in the NGFW market. Their solutions are built on a proprietary single-pass architecture that maximizes throughput while minimizing latency. What sets Palo Alto apart is its deep integration of application, user, and device-level data into its policy enforcement model.
Key architectural elements include:
- App-ID: Provides visibility and control over applications by classifying traffic based on application signatures.
- Content-ID: Offers threat prevention by scanning traffic for malware, exploits, and data leaks in real-time.
- User-ID: Associates network activity with specific users, enabling granular policy enforcement.
- Device-ID: Identifies endpoints to apply device-specific policies, improving control in BYOD environments.
These features work in concert to deliver a layered defense strategy, giving network administrators a clearer understanding of what’s happening in their environment.
Fortinet FortiGate: Security at Scale
Fortinet’s FortiGate NGFW stands as a powerful solution tailored to meet the evolving cybersecurity demands of modern organizations. With the ever-increasing complexity of enterprise networks, spanning hybrid environments, remote workforces, and cloud adoption, FortiGate’s focus on scalability, performance, and integration has made it a cornerstone of many global IT infrastructures. It forms the foundation of Fortinet’s broader Security Fabric, enabling consistent and intelligent security across a wide range of deployment scenarios.
Let’s dive deeper into the capabilities that make FortiGate a dominant force in the world of next-generation firewalls.
Hyperscale Security: Purpose-Built for Performance
At the heart of FortiGate’s strength is its commitment to hyperscale security. Modern businesses operate across expansive cloud and on-prem environments, serving thousands of users and processing vast amounts of data in real-time. Traditional security appliances often struggle under such loads. FortiGate addresses this challenge with purpose-built Security Processing Units (SPUs) and network processors like the NP7, which drastically enhance throughput and reduce latency, even with deep inspection features enabled.
These custom ASIC chips allow FortiGate to process encrypted traffic, perform SSL/TLS inspection, and run simultaneous security features, such as antivirus, IPS, and DDoS mitigation, without compromising speed or reliability. This ensures consistent performance in high-bandwidth environments like:
- Telecom and ISP data centers
- Multi-tenant hosting services
- High-frequency trading platforms
- National-scale educational networks
Whether handling 5,000 or 500,000 sessions, FortiGate’s hyperscale architecture can accommodate the increasing demands of digital transformation and distributed infrastructures.
Security Fabric Integration: A Unified Ecosystem
One of Fortinet’s standout innovations is its Security Fabric architecture. This concept extends beyond just NGFW functionality and instead connects Fortinet’s wide array of products, such as FortiSwitch, FortiAP, FortiClient, FortiSIEM, and FortiAnalyzer, into a cohesive, intelligent ecosystem.
By integrating these products, the Security Fabric allows organizations to:
- Share threat intelligence across endpoints, firewalls, and cloud platforms
- Automate incident response and remediation based on shared telemetry
- Visualize lateral movement or attack patterns in real-time
- Enforce consistent security policies across physical, virtual, and cloud environments
The Security Fabric also supports open standards and APIs, allowing third-party tools to participate in its threat-sharing and policy orchestration. This level of interoperability makes Fortinet an ideal choice for enterprises looking to build secure, manageable, and scalable security architectures without getting locked into proprietary silos.
Natively Integrated Proxy: A Gateway to ZTNA and SASE
As workforces become increasingly distributed and applications migrate to the cloud, organizations need to adopt Zero Trust Network Access (ZTNA) and Secure Access Service Edge (SASE) models. FortiGate supports both by offering natively integrated proxy capabilities directly within the NGFW.
Instead of relying on external proxies or third-party cloud brokers, FortiGate appliances can:
- Authenticate users and endpoints before granting access
- Inspect encrypted application traffic for threats and compliance violations
- Apply identity- and device-based policies for dynamic access control
- Segment application access based on user roles or risk profiles
For example, a remote contractor can be granted limited access to specific internal applications without exposing the full network. By embedding ZTNA controls at the firewall level, Fortinet provides a more seamless and secure experience for end users while maintaining centralized control for IT teams.
This proxy integration also supports SASE frameworks, allowing organizations to converge network and security services into a cloud-delivered architecture that’s optimized for remote access, mobile users, and hybrid cloud operations.
Automation-Driven Management: Operational Efficiency at Scale
Managing security across hundreds or thousands of endpoints and network segments can be a daunting task. That’s why Fortinet prioritizes automation and orchestration as part of its core FortiGate experience.
FortiOS, the underlying operating system of FortiGate, includes built-in automation features that enable:
- Automated response to predefined security events (e.g., quarantine infected devices)
- Dynamic policy updates based on threat intelligence
- Scheduled backups, configuration changes, and firmware upgrades
- Integration with ITSM systems, SIEM platforms, and cloud security tools
The FortiManager and FortiAnalyzer tools further enhance operational control. FortiManager offers a centralized management platform for policy creation, version control, and device lifecycle management. Meanwhile, FortiAnalyzer provides detailed reporting, log aggregation, and forensic insights, helping SOC teams make informed decisions.
By automating routine security operations, FortiGate reduces administrative overhead, lowers the risk of human error, and ensures faster response times during critical incidents.
Real-World Deployment Flexibility
FortiGate NGFWs are designed for deployment flexibility. Organizations can choose from a range of physical appliances, virtual firewalls (FortiGate-VM), or cloud-native options based on their architecture.
- Physical Appliances: Ideal for branch offices, headquarters, and data centers. Models range from compact FortiGate 40F to high-end FortiGate 7121F.
- Virtual Appliances: FortiGate-VM supports private clouds like VMware and Hyper-V, and public clouds like AWS, Azure, and GCP. It’s ideal for cloud interconnects and east-west traffic protection.
- Container Firewalls: Fortinet also offers firewall container solutions for Kubernetes environments, enabling microsegmentation and workload isolation in container-native platforms.
- Cloud-Native Integrations: Fortinet’s Security-as-a-Service offerings integrate with cloud providers for functions like web application firewalling, API protection, and cloud access security brokerage (CASB).
This flexibility ensures that FortiGate can fit into any network topology or digital transformation roadmap. Whether you’re securing branch offices, expanding into multicloud, or operating a service provider backbone, FortiGate can scale with your infrastructure.
Compliance and Industry Use Cases
FortiGate is widely used across industries, especially in compliance-driven environments where granular access controls, encrypted traffic inspection, and audit logging are mandatory.
Common sectors using FortiGate include:
- Healthcare: For HIPAA compliance, secure EHR access, and endpoint protection.
- Finance: For PCI-DSS compliance, transaction security, and fraud detection.
- Education: For CIPA compliance and content filtering in K–12 environments.
- Retail: For branch security, POS system protection, and network segmentation.
- Manufacturing: For securing industrial control systems (ICS) and OT environments.
FortiGate includes built-in tools for audit trail logging, role-based access controls, and compliance reporting, making it a go-to choice for organizations with strict regulatory obligations.
Training and Certification Support
Managing FortiGate firewalls requires skilled professionals, and Fortinet provides a full certification track to prepare network and security engineers. The NSE (Network Security Expert) program ranges from beginner to expert levels:
- NSE 1–3: Foundational cybersecurity awareness
- NSE 4: FortiGate security and infrastructure fundamentals
- NSE 5–6: Advanced configuration, analytics, and management
- NSE 7–8: Enterprise-level architecture, troubleshooting, and expert operations
To assist professionals in passing these certifications, platforms like Exam-Labs offer high-quality practice tests, scenario-based labs, and study materials. These resources simulate real-world environments, making it easier to understand FortiGate’s interface, configuration options, and policy management.
Using Exam-Labs for NSE preparation not only helps candidates validate their knowledge but also builds operational readiness for deploying Fortinet solutions in production environments.
The emphasis on deep integration and orchestration across the entire attack surface has made Fortinet a go-to solution for organizations seeking end-to-end security without high complexity.
Market Recognition and Leadership
Both Palo Alto and Fortinet have consistently appeared in the Gartner Magic Quadrant for Network Firewalls. Fortinet was recognized as a leader in 2021 due to its strong feature set and ability to execute across multiple verticals. Palo Alto has also earned accolades for its innovation and consistent performance in independent tests like NSS Labs.
While Fortinet generally appeals to cost-conscious buyers who still want premium features, Palo Alto caters to organizations that require high assurance, advanced threat analytics, and cutting-edge technology regardless of cost.
Industry Use Cases
Palo Alto NGFWs are often deployed in:
- Financial institutions requiring strict compliance and audit trails
- Government agencies with sensitive data handling needs
- Large enterprises with diverse cloud, on-prem, and hybrid infrastructure
Fortinet FortiGate is ideal for:
- Educational institutions and SMEs with limited IT staff
- Branch offices and distributed networks needing scalable solutions
- Managed service providers offering security as a service
While their deployments may overlap, their architectural differences and strategic focus points usually determine which firewall fits best for a given scenario.
Licensing and Support Model
Palo Alto uses a modular licensing model where features like Threat Prevention, URL Filtering, WildFire, and DNS Security can be licensed separately or bundled. Support is available through various levels of service agreements, offering access to updates, technical support, and cloud-based analytics.
Fortinet simplifies things with bundles like FortiGuard and FortiCare, offering services such as antivirus, IPS, web filtering, and 24/7 support in a single package. This makes budgeting easier and ensures that smaller organizations can access enterprise-level protection without a steep learning curve.
Training and Certification Pathways
To support the effective deployment and maintenance of their firewalls, both companies offer certifications and training. If you’re preparing for Palo Alto or Fortinet exams, hands-on practice is essential. This is where platforms like Exam-Labs come in. They provide practice tests, exam dumps, and simulation environments that mimic real-world scenarios. Whether you’re aiming for the Palo Alto Networks Certified Network Security Engineer (PCNSE) or the Fortinet NSE series, training via Exam-Labs can bridge the gap between theory and real-world execution.
With real exam-style questions and updated study material, Exam-Labs helps reduce test anxiety while boosting retention. Professionals often use these tools to supplement their learning and reinforce critical concepts before sitting for the actual certification exam.
Summary of Strengths
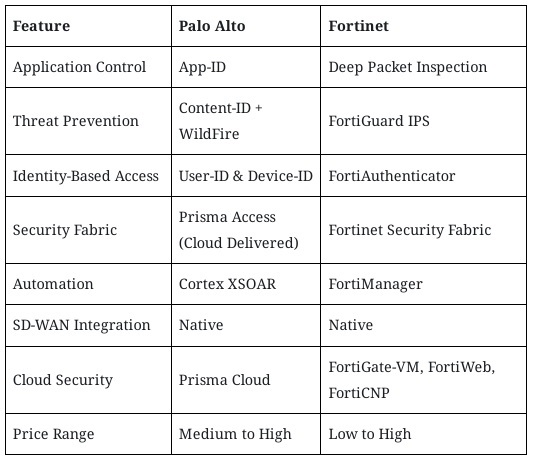
This foundational comparison sets the stage for the next part in the series, where we’ll explore a deeper, feature-by-feature evaluation of these firewalls, focusing on how they stack up in categories such as threat detection, application control, identity management, and scalability.
Feature-by-Feature Comparison – Application Control, Threat Prevention, and Security Fabric
Choosing between Palo Alto Networks and Fortinet’s FortiGate for next-generation firewall (NGFW) deployment involves more than just brand loyalty or pricing. It demands a detailed evaluation of the individual features that define the value and efficacy of the solution. In this part, we’ll dissect the most critical NGFW features that influence network protection: application control, threat prevention, identity-based access, and integrated security fabric.
Application Control: App-ID vs Deep Inspection
Application visibility is a cornerstone of next-generation firewalls. In legacy firewalls, policies were enforced primarily based on port numbers and IP addresses. But modern applications use dynamic ports, encryption, and evasion tactics. Hence, NGFWs must understand the application itself, not just the wrapper.
Palo Alto Networks introduced App-ID, a proprietary engine that identifies applications regardless of port, protocol, encryption (SSL/TLS), or evasive tactics. App-ID inspects traffic packets across all layers and determines exactly what application is being used. This allows administrators to apply policy controls at the application level, such as allowing Slack for the marketing department but blocking file uploads within the app.
The engine is updated frequently via threat intelligence feeds, ensuring new applications and behaviors are recognized. This level of granularity significantly reduces the attack surface.
Fortinet FortiGate uses a robust application control engine that leverages a combination of signatures, behavioral analytics, and heuristics to identify applications. While it may not have a proprietary term like App-ID, Fortinet’s engine is powerful and scalable, especially when paired with FortiGuard Labs’ threat feeds.
The key difference lies in Palo Alto’s contextual depth. Its identification not only classifies the app but also drills into functionality, e.g., distinguishing between Dropbox login vs upload activity. Fortinet’s engine is fast and efficient, making it ideal for high-throughput environments but may offer less fine-grained control in certain use cases.
Threat Prevention: Single-Pass vs Multi-Scan Processing
Threat prevention in NGFWs includes antivirus scanning, intrusion prevention (IPS), anti-spyware, malware sandboxing, and DNS filtering. The underlying architecture heavily influences the firewall’s ability to deliver high throughput without sacrificing security.
Palo Alto uses a single-pass parallel processing architecture, meaning traffic is scanned once for multiple security functions, including IPS, URL filtering, and malware detection. This drastically reduces latency while improving CPU efficiency.
Its Content-ID engine integrates with WildFire, Palo Alto’s malware analysis cloud, to detect zero-day threats in real-time. DNS Security and Advanced URL Filtering use machine learning to detect and block evolving threats based on behavior analysis, reputation, and URL categorization.
Fortinet applies multiple engines depending on the enabled features. The FortiGuard Security Services bundle includes real-time updates for IPS, antivirus, DNS filtering, and web filtering. The FortiSandbox service provides an additional layer for advanced malware analysis, while inline blocking ensures threats are stopped before they reach the endpoint.
One architectural advantage of Fortinet is its use of purpose-built ASIC chips (e.g., NP7) in some appliances, accelerating performance even when many security services are enabled.
However, Fortinet’s performance may fluctuate when multiple services are turned on simultaneously, particularly in lower-end models. Palo Alto’s consistent throughput, thanks to single-pass scanning, gives it an edge in environments that require simultaneous, deep-layer security without compromising performance.
Identity-Based Access: User and Device Context
Firewall policies based on users and devices rather than IP addresses improve visibility and control, especially in dynamic environments like hybrid workplaces or cloud deployments.
Palo Alto offers User-ID and Device-ID, providing a dual-context model. User-ID integrates with Active Directory, LDAP, and SAML to associate traffic with users. Device-ID classifies traffic based on endpoint attributes, including device type, OS, and compliance posture.
This enables policies like “Allow all Android devices from HR department to access internal CRM over VPN, but block if OS version is outdated.” The ability to write policies that follow users and devices across networks is extremely beneficial in remote work scenarios.
Fortinet counters with FortiAuthenticator and FortiClient, which combine to deliver identity and device context. FortiAuthenticator pulls data from AD, RADIUS, and SAML sources, while FortiClient offers endpoint posture checks and telemetry. With ZTNA capabilities, Fortinet enables device-based conditional access.
Though both platforms are competitive in identity-based access, Palo Alto’s deep integration into its policy engine and cloud infrastructure gives it a seamless advantage in multi-cloud and zero-trust environments. Fortinet’s solution is highly effective but may require additional configuration and licenses.
Unified Security Fabric and Ecosystem Integration
A firewall is only one part of an organization’s defense. NGFWs must integrate with endpoint protection, threat intelligence, cloud access security brokers (CASBs), and security operations platforms. Ecosystem integration determines how well a firewall scales across use cases like remote access, cloud workload protection, or branch security.
Fortinet’s Security Fabric is a major selling point. It provides centralized visibility, policy orchestration, and intelligence sharing across all Fortinet products: firewalls, endpoints, switches, Wi-Fi, and even third-party products through open APIs. This ecosystem strategy simplifies operations and enhances threat correlation.
FortiManager and FortiAnalyzer tools further enhance this integration with robust logging, automation scripts, and forensic analysis capabilities. The Security Fabric also powers Fortinet’s secure SD-WAN, ZTNA, and OT security solutions.
Palo Alto Networks takes a platform approach with its Prisma Access, Cortex XSOAR, and Prisma Cloud. Prisma Access offers SASE services, while Cortex XSOAR delivers SOAR capabilities for automated incident response. Everything ties back to the NGFW, feeding telemetry into a unified data lake that supports AI-powered detection and policy generation.
This allows Palo Alto customers to manage their cloud, network, and endpoint security through a single-pane-of-glass interface, with predictive analytics guiding decision-making.
While both companies offer extensive integrations, the key distinction lies in intent. Fortinet builds a vertically integrated system—buy everything from Fortinet for maximum benefit. Palo Alto emphasizes horizontal extensibility—integrate with many environments and third-party tools while maintaining a high-security baseline.
Real-World Threat Detection Scores
Independent tests such as those by NSS Labs and CyberRatings.org help validate claims of threat prevention capabilities. While Palo Alto and Fortinet have both scored highly, recent results give Palo Alto a slight edge.
- Palo Alto: 97.87% block rate (NSS Labs), with low false positives and stable throughput under load.
- Fortinet: 99.3% detection rate (CyberRatings), but performance may vary based on configuration and enabled services.
These scores suggest both platforms are highly effective, but Palo Alto is often preferred in environments where zero-day protection and predictability under load are critical.
Security and Compliance Features
Palo Alto focuses on:
- DNS Security with predictive analytics
- Industry-first cloud-delivered Data Loss Prevention (DLP)
- Secure 5G-native network integration
- URL filtering with real-time behavioral updates
Fortinet delivers:
- Web, content, and device security
- Hybrid and multi-cloud protection
- SSL inspection and compliance features
- Endpoint threat intelligence and response
The feature diversity makes both firewalls suitable for compliance-heavy industries like healthcare, finance, and critical infrastructure. However, Palo Alto’s native support for more compliance frameworks gives it a slight edge in audit-heavy environments.
Integration with Exam-Labs for Training and Readiness
Both firewalls require trained professionals for deployment and management. Certification programs like PCNSE (for Palo Alto) and NSE 4–NSE 8 (for Fortinet) test the depth of a candidate’s understanding.
Aspiring security engineers often turn to platforms like Exam-Labs, which offer updated practice tests, simulation questions, and downloadable content aligned with real exam objectives. These resources are particularly useful for identifying weak areas before investing in official training courses. Practicing on real-world scenarios through Exam-Labs can help solidify your knowledge and improve your chances of passing high-stakes exams.
Performance, Scalability, and Management – Which NGFW Delivers Best in Practice
Selecting the best next-generation firewall (NGFW) is not just about checking feature lists. In real-world environments, it comes down to performance under pressure, scalability across infrastructure, and how intuitive or complex the management tools are. This part of the series dives into how Palo Alto Networks and Fortinet’s FortiGate compare when it comes to throughput, latency, high availability, cloud-native support, and centralized control.
Throughput and Real-World Performance
Throughput refers to how much traffic a firewall can process without dropping packets or slowing down. It’s one of the most critical metrics for organizations with high bandwidth needs or strict performance SLAs.
Palo Alto Networks firewalls are built with a single-pass architecture. This design allows all traffic to be processed once through the inspection engines, App-ID, Content-ID, User-ID, and threat detection modules, without duplicating effort. This method significantly reduces CPU cycles and latency.
In NSS Labs testing, Palo Alto demonstrated an average throughput of 7888 Mbps with all security features enabled. Even with heavy SSL traffic or multiple scanning functions in place, Palo Alto systems consistently maintain low latency and high availability.
Fortinet FortiGate takes a different approach by utilizing purpose-built ASIC processors in many of its appliances. These hardware accelerators boost packet processing, making Fortinet firewalls among the fastest NGFWs on the market. For example, FortiGate 500E scored a strong 6753 Mbps in independent tests.
However, Fortinet’s performance can fluctuate depending on which security services are enabled. While the hardware excels at raw throughput, enabling deep packet inspection, application control, and logging may reduce performance in lower-end models. High-end FortiGate appliances balance these tasks more effectively.
For most mid-market enterprises, both firewalls offer more than enough speed. But in ultra-low latency environments, such as financial services or telecommunications, Palo Alto’s architecture may provide more consistent performance under full inspection workloads.
Latency and Packet Handling
Network latency directly impacts the end-user experience, particularly with real-time applications like video conferencing, VoIP, and cloud-hosted productivity tools.
Palo Alto NGFWs are known for maintaining low latency even with multiple inspection layers active. Their architecture minimizes state transitions between engines and uses intelligent routing to ensure packets are inspected only once.
Fortinet FortiGate offers excellent latency performance as well, thanks to its custom ASIC chips. These are engineered specifically for network security functions and help the firewall maintain microsecond-level latency even when handling encrypted traffic.
However, latency can increase slightly when many advanced threat prevention modules are enabled simultaneously, especially on smaller Fortinet devices. Palo Alto tends to be more consistent under full load.
High Availability and Redundancy
Downtime is expensive. Both vendors offer high availability (HA) features, including active-active and active-passive failover, session synchronization, and link monitoring.
Palo Alto supports stateful HA with synchronization of session tables, configuration settings, and policy updates. Devices can switch between HA peers almost instantly. Administrators can configure path monitoring to ensure HA pairs are aware of link failures and reroute traffic accordingly.
Fortinet provides flexible HA options with straightforward configuration. FortiGate’s Virtual Clustering Protocol (VCluster) can be used to manage multiple VDOMs (virtual domains) independently, even in HA mode. This provides robust isolation between departments or tenants and reduces blast radius in the event of failure.
Both platforms offer similar uptime guarantees, but Palo Alto slightly edges ahead in large-scale deployments requiring granular failover controls and seamless user experience during transitions.
Scalability in Hybrid and Multi-Cloud Environments
As more organizations adopt multi-cloud strategies, the ability of an NGFW to operate consistently across AWS, Azure, GCP, and on-prem infrastructure is critical.
Palo Alto’s cloud-centric strategy is well-executed through Prisma Access and VM-Series firewalls. Prisma Access enables secure access to cloud applications with SASE capabilities, while the VM-Series provides virtualized NGFWs that integrate with major cloud providers. These firewalls offer uniform policy management, centralized logging, and cloud-native API hooks for automation.
Fortinet also supports hybrid cloud environments via FortiGate-VM and FortiCNP. FortiCNP provides continuous posture monitoring in cloud-native environments, while FortiGate-VM integrates with tools like Terraform and Ansible for DevOps automation.
In scalability, both vendors offer robust options. However, Palo Alto’s deeper alignment with modern DevSecOps pipelines and native support for microsegmentation in Kubernetes clusters gives it an edge in high-scale, cloud-native environments.
Centralized Management and Usability
Ease of management can make or break a firewall deployment. A powerful device becomes burdensome if the interface is clunky or difficult to navigate.
Palo Alto provides a unified console via Panorama, which manages multiple firewalls and devices across various locations. Panorama offers rich visualizations, role-based access control, change tracking, and deep analytics. It also supports multi-tenancy and simplifies auditing across networks.
Palo Alto’s interface, whether via the web or CLI, is intuitive and consistent. Configuration wizards assist new admins, while advanced users benefit from robust scripting capabilities for bulk changes and policy automation.
Fortinet offers FortiManager and FortiAnalyzer as its centralized management tools. FortiManager is well-suited for managing dozens or even thousands of devices. It supports automation scripts, bulk configuration, dynamic policy packages, and advanced device grouping.
FortiAnalyzer provides deep logging, forensic analysis, and incident correlation. Together, these tools form the backbone of Fortinet’s Security Fabric and are highly effective for managed service providers or large enterprises.
While Fortinet’s tools are comprehensive, they may require more onboarding and familiarity than Palo Alto’s Panorama. That said, experienced admins will appreciate the power and flexibility they offer.
Automation and Orchestration
Modern security demands automation. Manual intervention for every alert or configuration change is inefficient and risky.
Palo Alto leverages Cortex XSOAR, its Security Orchestration, Automation, and Response (SOAR) platform. It allows SOC teams to build playbooks that automatically respond to alerts, fetch threat intel, and adjust firewall rules as needed. Cortex XSOAR integrates seamlessly with Palo Alto NGFWs for auto-remediation.
Fortinet integrates automation through FortiOS and FortiSOAR. These platforms allow administrators to set triggers, define workflows, and connect with external APIs. FortiSOAR centralizes alert management and incident response while pulling data from the entire Fortinet Security Fabric.
Both vendors support REST APIs, SNMP, syslog, and other integrations. Palo Alto tends to offer more out-of-the-box playbooks for automation, while Fortinet is flexible for custom scripting and in-house development.
Licensing Complexity and Upgrade Paths
Firewall licensing can be confusing, with different tiers, services, and support levels. Clarity in licensing affects long-term costs and scalability.
Palo Alto typically breaks its services into individual subscriptions: Threat Prevention, DNS Security, WildFire, and GlobalProtect. This modular approach allows organizations to pay only for what they need but can lead to complexity when scaling across multiple sites.
Fortinet simplifies licensing by bundling services into packages like FortiGuard UTM Bundle and Enterprise Protection Bundle. These include web filtering, application control, antivirus, and more. For most customers, this approach is more predictable and easier to manage.
For cloud environments, both vendors offer BYOL (Bring Your Own License) and pay-as-you-go models. They also support autoscaling deployments, making licensing flexible for dynamic workloads.
Study Resources and Performance Labs
Preparing to deploy either of these firewalls requires hands-on training. Certifications like Palo Alto’s PCNSE or Fortinet’s NSE 4, 5, and 7 are highly valued.
Exam-Labs offers high-quality practice tests and simulated labs that help candidates test their skills under exam-like conditions. These resources are invaluable for mastering deployment, policy creation, and troubleshooting scenarios. For example, engineers can simulate configuring HA clusters or test failover logic using Exam-Labs’ practice content.
With updated content, detailed explanations, and a format that mimics real-world exam objectives, Exam-Labs continues to be a top resource for both aspiring and experienced professionals working with these firewall platforms.
Pricing, Use Cases, and Final Verdict – Choosing the Right NGFW for Your Organization
In this final part of the series comparing Palo Alto Networks and Fortinet NGFWs, we’ll evaluate pricing strategies, deployment use cases, support considerations, and help you decide which firewall platform best suits your business. While both companies offer industry-leading security solutions, your decision should be based on organizational priorities such as cost, complexity, compliance requirements, cloud strategy, and available resources.
Cost Comparison: Entry-Level to Enterprise Scale
Price is one of the biggest differentiators between Fortinet and Palo Alto. Both offer a wide range of firewall models, but their pricing strategies reflect different market targets.
Fortinet FortiGate is well-known for its affordability, especially in entry-level appliances. You can expect to pay:
- Around $700–$1,200 for small business appliances like FortiGate 40F or 60F.
- $7,000–$23,000 for enterprise-grade firewalls like the FortiGate 500E.
- Up to $350,000 for high-end chassis models like the FortiGate 7060E-8.
Fortinet’s licensing bundles like UTM Protection Bundle or Enterprise Bundle simplify budgeting. Each bundle includes multiple services like antivirus, web filtering, IPS, and FortiCare support. Customers can choose between 1-year, 3-year, or custom terms, allowing for flexibility and cost efficiency.
Palo Alto Networks firewalls tend to be more expensive upfront. A typical cost structure includes:
- $3,500–$6,000 for entry-level appliances like the PA-220 or PA-440.
- $20,000–$200,000+ for enterprise appliances depending on capacity, subscriptions, and support tiers.
Licenses are modular. Services such as Threat Prevention, WildFire, DNS Security, and GlobalProtect are billed separately unless bundled. This a la carte model allows precise customization but can lead to higher total costs over time, especially when scaling.
For organizations with limited budgets, Fortinet offers excellent value. But for security-conscious enterprises that demand maximum control and consistency, Palo Alto’s pricing reflects its premium capabilities.
Use Case Scenarios
The choice between Palo Alto and Fortinet often boils down to how the firewall will be used. Each platform shines in specific environments.
1. Small Businesses and Branch Offices
- Best Option: Fortinet Fortinet’s smaller devices are affordable, fast, and easy to deploy. The centralized management via FortiCloud makes them attractive to organizations with minimal IT staff. Its all-in-one security features in a single appliance simplify security operations.
2. Large Enterprises and Data Centers
- Best Option: Palo Alto With consistent performance, a modular security model, and rich threat intelligence, Palo Alto is ideal for large-scale networks with complex policies. Its single-pass architecture ensures high throughput and reduced latency, which is vital in high-demand environments.
3. Cloud-Native and Hybrid Environments
- Best Option: Palo Alto Palo Alto’s Prisma Cloud and VM-Series firewalls are built for cloud-native deployments, integrating seamlessly with AWS, Azure, and GCP. Features like microsegmentation, automation via Terraform, and container security make it a top choice for DevSecOps teams.
4. Managed Service Providers (MSPs)
- Best Option: Fortinet Fortinet’s scalable licensing and Security Fabric ecosystem are well-suited for MSPs managing multiple clients. The combination of FortiManager, FortiAnalyzer, and flexible VDOMs allows robust multi-tenant support.
5. Education and Nonprofits
- Best Option: Fortinet Budget constraints are common in schools and nonprofit organizations. Fortinet’s cost-effective solutions, along with academic discounts, make it a natural fit for these sectors. Basic NGFW functions, content filtering, and Wi-Fi integration support education use cases well.
Support and Maintenance
Ongoing support is critical for firewall operations. Both vendors provide tiered support programs with SLAs, 24/7 help desks, hardware replacement, firmware updates, and access to threat intelligence.
Palo Alto support levels include Standard, Premium, and Premium Plus, with options for dedicated technical account managers. The support model is structured and enterprise-friendly but priced accordingly.
Fortinet offers FortiCare support options ranging from 8×5 hardware support to 24×7 enhanced support. Subscriptions to FortiGuard threat intelligence ensure real-time updates for antivirus, IPS, and URL filtering.
While Palo Alto offers more tailored enterprise support, Fortinet’s service model is simple, fast, and cost-effective—ideal for growing organizations.
Training, Certification, and Staffing
The complexity of managing either platform depends largely on your internal skill set. Certification training is highly recommended.
Palo Alto’s PCNSE (Palo Alto Networks Certified Network Security Engineer) is the standard credential for firewall admins. To prepare, professionals often rely on Exam-Labs for practice tests that simulate real-world configuration tasks, log analysis, and incident response.
Fortinet’s NSE Certification Track spans from NSE 1–8, offering a structured path from foundational knowledge to advanced troubleshooting. Exam-Labs also provides full support for these exams through scenario-based practice content.
When building a team or outsourcing to a provider, make sure candidates are certified. These certifications not only ensure competence but can reduce downtime, improve policy enforcement, and lower risk.
Community, Ecosystem, and Innovation
Palo Alto’s innovation engine is fueled by acquisitions and research. Prisma Access, Cortex XSOAR, and WildFire represent just a few advanced technologies integrated into its firewall platform. The Palo Alto user community is active, with a large knowledge base, forums, and third-party tool support.
Fortinet’s innovation is driven by its unified ecosystem. The Fortinet Security Fabric integrates firewalls, SD-WAN, EDR, cloud access, and wireless APs in one orchestrated network. Its commitment to automation, low-cost scaling, and open APIs makes it appealing to security engineers and architects alike.
Final Verdict: Which NGFW Is Right for You?
Choosing the right NGFW comes down to your priorities. Below is a breakdown of key decision factors:
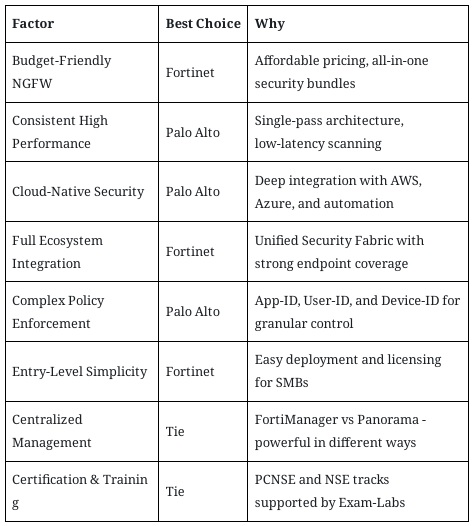
For organizations prioritizing advanced security, deep cloud integration, and premium support, Palo Alto is a future-proof investment. For cost-conscious businesses, especially those growing quickly or managing many locations, Fortinet offers exceptional value without sacrificing performance.
Final Thoughts
Both Palo Alto and Fortinet are world-class NGFW providers. Your specific business goals, IT environment, and risk posture will ultimately shape the best path forward. Make sure to evaluate your current needs, future scalability, and internal expertise when selecting between the two.
Before implementing either solution, it’s highly recommended to complete vendor certifications. Resources like Exam-Labs provide accurate practice tests and simulations that can help your team prepare for deployment, reduce configuration errors, and maximize ROI from your firewall investment.
Whichever you choose, a modern NGFW is no longer optional, it’s the front line of defense for every connected organization.
