Cybersecurity architects are responsible for the overall design and implementation of secure networks, applications, and infrastructures. They must understand business needs, regulatory requirements, and security best practices. They also need to coordinate with multiple departments, from C-suite executives to operations teams, making certifications that include governance, compliance, and communication strategies especially useful.
Certifications do more than decorate a resume. They:
- Validate your knowledge with industry-recognized standards
- Demonstrate commitment to professional development
- Offer structured paths to gain real-world, applicable skills
- Boost credibility with peers and hiring managers
- Open doors to new job opportunities and higher salary tiers
With that in mind, let’s dive into the certifications that are most relevant to a future or current cybersecurity architect.
1. Microsoft Certified: Cybersecurity Architect Expert (SC-100) – A Comprehensive Guide
The Microsoft Certified: Cybersecurity Architect Expert (SC-100) is quickly emerging as one of the most sought-after certifications for professionals aiming to advance their careers in cybersecurity architecture and strategy. Designed by Microsoft to align with the latest enterprise security practices and cloud security demands, SC-100 provides a robust framework for securing hybrid environments, managing enterprise risk, and integrating defense-in-depth approaches across technologies and teams.
Whether you’re working as a cloud security engineer, security consultant, or aspiring to become a cybersecurity architect or CISO, this certification validates your ability to design and implement comprehensive, future-proof security strategies across diverse digital infrastructures.
What Is SC-100 All About?
The SC-100 certification assesses your skills in designing a cybersecurity strategy that protects cloud, hybrid, and on-premises infrastructures. Rather than focusing on a single Microsoft product, it evaluates your ability to build end-to-end security models using the full suite of Microsoft security solutions while incorporating zero trust principles, compliance strategies, and enterprise-wide governance.
Core Competencies:
- Designing Zero Trust architectures for enterprise systems
- Evaluating and interpreting governance, risk, and compliance (GRC) frameworks
- Aligning security strategies with business goals and regulatory requirements
- Managing identity, endpoint, application, and network security at scale
- Integrating Microsoft Defender, Azure Sentinel, Microsoft Entra (Azure AD), and Microsoft Purview
Prerequisites and Ideal Candidates
Unlike many other Microsoft certifications, SC-100 is considered an Expert-level credential. Microsoft recommends that candidates have one or more of the following associate-level certifications before attempting SC-100:
- Microsoft Certified: Security Operations Analyst Associate (SC-200)
- Microsoft Certified: Identity and Access Administrator Associate (SC-300)
- Microsoft Certified: Information Protection Administrator Associate (SC-400)
- Microsoft Certified: Azure Security Engineer Associate (AZ-500)
Although not mandatory, holding at least one of these certifications significantly improves your readiness by giving you a technical foundation in Microsoft’s core security products.
This certification is ideal for professionals who:
- Are responsible for planning and implementing cybersecurity policies
- Collaborate with stakeholders across IT, operations, and compliance
- Lead or manage teams responsible for security tool integration
- Are transitioning from hands-on engineering to architectural roles
- Want to align Microsoft cloud security with enterprise security strategy
Exam Details
- Exam Code: SC-100
- Title: Microsoft Cybersecurity Architect
- Length: Approximately 100–120 minutes
- Format: Multiple choice, scenario-based, drag and drop, and case study questions
- Passing Score: 700 out of 1000
- Cost: $165 USD (subject to change by region)
The SC-100 exam is divided into four functional areas, each representing a critical component of modern security architecture.
Exam Domains
1. Design a Zero Trust strategy and architecture (30–35%)
This domain covers:
- Identity and access management
- Network segmentation and perimeter defense
- Application security planning
- Threat detection and response workflows
- Implementing defense-in-depth at all levels
Zero Trust is not just a buzzword. It’s a core operating principle in modern security design, and this domain ensures you know how to apply it practically across Microsoft environments.
2. Evaluate Governance Risk Compliance (GRC) technical strategies and security operations strategies (20–25%)
You’ll be tested on your ability to:
- Interpret compliance requirements and map them to technical implementations
- Evaluate data protection strategies
- Integrate Microsoft Purview Information Protection and Microsoft Defender for Cloud
- Develop a comprehensive risk management strategy aligned with NIST, ISO, and GDPR
This domain ensures architects can bridge technical designs with regulatory mandates, working with legal, HR, and data governance teams to ensure compliance.
3. Design security for infrastructure (20–25%)
Key topics include:
- Securing virtual machines, containers, and Kubernetes workloads
- Evaluating firewalls, policies, and security configurations for hybrid environments
- Ensuring least privilege access across services
- Integrating Microsoft Defender for Endpoint and Microsoft Defender for Cloud
Expect scenario-based questions that simulate real-world hybrid infrastructure environments.
4. Design a strategy for securing data and applications (20–25%)
This domain focuses on:
- Application lifecycle security
- Microsoft Purview for data governance
- Threat modeling and secure software design
- Encryption practices for data at rest, in motion, and in use
Here, the goal is to ensure you understand how to secure both structured and unstructured data while maintaining business productivity.
Study Strategy and Resources
Preparing for the SC-100 exam requires a combination of conceptual learning and practical application. Many professionals spend 6 to 8 weeks preparing, depending on their familiarity with Microsoft security solutions.
Step-by-Step Study Plan:
- Understand the Exam Blueprint
Download the official Microsoft SC-100 exam skills outline and use it to guide your study plan. - Use Exam-Labs for Practice Exams and Scenarios
Exam-Labs offers a rich library of SC-100-specific practice questions, flashcards, and timed mock exams that simulate the actual exam environment. These tools help build confidence and reinforce your understanding of key concepts. - Hands-On Practice in Microsoft Azure Portal
Get real-world experience by creating trial tenants and configuring:- Conditional Access Policies
- Microsoft Sentinel Workbooks
- Microsoft Defender for Identity alerts
- Compliance Manager assessments
- Watch Official Microsoft Learn Modules
These free modules provide deep dives into every product mentioned in the exam – perfect for self-paced learning. - Join Study Groups
LinkedIn and Reddit communities (such as r/AzureCertification) offer discussion threads, updates, and peer support.
Real-World Benefits of SC-100 Certification
1. Industry Recognition
Holding SC-100 positions you as a thought leader in cloud security design. Many enterprises are adopting Microsoft security tools, and this certification proves you can orchestrate secure digital transformation initiatives.
2. Enhanced Career Mobility
Certified cybersecurity architects are in high demand. Roles you may qualify for include:
- Cybersecurity Architect
- Cloud Security Consultant
- Security Solutions Designer
- Enterprise Security Strategist
- Security Practice Lead
3. Salary Potential
Professionals holding SC-100 can expect salaries ranging from:
- $130,000 to $170,000 in North America
- $95,000 to $145,000 in Europe and APAC regions
These numbers increase significantly with additional certifications like CISSP or CCSP, and with experience in cross-cloud environments (Azure, AWS, GCP).
4. Cross-Departmental Influence
SC-100 certified professionals often work closely with:
- Compliance officers
- Cloud architects
- DevOps leads
- C-level executives
This makes you a strategic voice in shaping business continuity and incident response frameworks.
Who Should Avoid SC-100?
Despite its strengths, SC-100 may not be the right certification for:
- Entry-level IT professionals with no Microsoft security experience
- Professionals looking for hands-on, tool-specific training (SC-200, SC-300 may be better entry points)
- Candidates focused solely on vendor-neutral certifications
This is a design and strategy certification, so a baseline understanding of Microsoft Defender, Azure policy, and cloud workloads is crucial.
Why It’s Important
As enterprises increasingly move to cloud environments, cybersecurity architects must be fluent in cloud-native and hybrid-cloud architectures. The SC-100 exam ensures that candidates understand security across cloud workloads, are familiar with compliance mandates, and can assess risks related to identity, devices, and data. These are critical skills for anyone building or evolving a secure ecosystem.
Preparation and Resources
To prepare for the SC-100, most professionals benefit from targeted study paths using platforms such as Exam-Labs, where they can access real-world simulations, SC-100 practice tests, and scenario-based quizzes. These tools ensure readiness by focusing on both Microsoft services and the broader architectural approach that security leaders must adopt.
Ideal For:
- Current or aspiring cybersecurity architects
- Cloud security engineers looking to move into strategic design roles
- CISOs or security leads building their Microsoft security ecosystem
- Professionals aiming for higher-level certifications like CISSP
2. CompTIA Security+: Building the Foundation
While the SC-100 targets advanced professionals, CompTIA Security+ is often the first certification that aspiring security architects earn. It establishes essential knowledge about security concepts, risk management, and best practices in various domains such as infrastructure, application security, and compliance.
Key Topics Covered
Security+ provides a foundational understanding of:
- Risk assessment and mitigation strategies
- Threat identification and response
- Secure network and architecture design
- Access management and cryptography
- Basic governance and compliance frameworks
Although Security+ does not delve deeply into architecture-specific planning, it ensures that candidates understand the fundamental building blocks of security, which is essential before progressing to architect-level certifications.
Why It’s Valuable
Every cybersecurity architect must be grounded in the fundamentals of security. Security+ bridges the gap between general IT knowledge and security specialization. It enables professionals to speak the language of security and provides an overview of how individual technologies and policies impact the larger organizational structure.
Additionally, Security+ is recognized by organizations worldwide and often required for government or defense-related positions.
Preparation Tips:
Because this is an entry-level certification, preparation is relatively straightforward. Most learners combine hands-on practice labs, reading study guides, and using platforms like Exam-Labs for up-to-date Security+ practice exams and topic reviews.
These resources allow candidates to not only pass the exam but also retain applicable skills they can use in the workplace.
Ideal For:
- IT professionals transitioning into cybersecurity
- Junior security analysts aiming to build technical credibility
- Professionals preparing for intermediate-level certifications
- Anyone looking to validate their core cybersecurity knowledge
Security+ and SC-100: A Perfect Certification Pairing
While these certifications serve different purposes, they are incredibly complementary. Security+ provides foundational skills and vocabulary, while SC-100 focuses on strategy, architecture, and leadership.
By completing both, professionals create a layered certification portfolio that demonstrates:
- Mastery of security fundamentals
- An understanding of modern enterprise security strategies
- Knowledge of identity, access, cloud, and compliance integration
- The ability to plan and execute secure digital transformation projects
This combination is particularly attractive to employers looking for well-rounded candidates who can evolve from technical implementers to security strategists.
Career Impact
Holding both Security+ and SC-100 places you in a strong position to pursue roles such as:
- Cybersecurity Architect
- Security Solutions Consultant
- Cloud Security Engineer
- Enterprise Risk Analyst
- Security Project Manager
You’ll be qualified to participate in planning meetings, contribute to architecture design, ensure regulatory compliance, and serve as the bridge between technical security teams and executive leadership.
With both certifications, professionals often see a salary increase of 15–25% depending on experience and industry. The added credentials make you more marketable, more promotable, and more trusted as a subject-matter expert.
Deepening Expertise with PenTest+ and CISSP
Cybersecurity architects wear many hats. They design enterprise-wide defense systems, ensure regulatory compliance, and coordinate with red and blue teams to proactively defend against evolving threats. To function effectively in such a multifaceted role, security architects need both technical mastery and leadership capability. While focused on foundational credentials like Microsoft SC-100 and CompTIA Security+, this will introduce you to two advanced certifications that strengthen offensive security skills and strategic design knowledge: CompTIA PenTest+ and CISSP.
These two certifications are ideal for cybersecurity professionals seeking to shift from operational security to architectural leadership roles. One will teach you how to think like an attacker; the other will teach you how to lead like a CISO.
The Evolving Role of a Cybersecurity Architect
Cybersecurity architects occupy a unique position at the intersection of technology, business, and risk management. As organizations become more digitally interconnected and threats grow in sophistication, the role of a cybersecurity architect has expanded beyond simple network defense. Today, they are expected to understand not only how to protect systems, but also why those systems are at risk, how business operations depend on them, and what strategies must be in place to protect them at scale.
Gone are the days when cybersecurity architects only dealt with firewalls, access controls, and intrusion prevention systems. Now, they are expected to lead conversations around zero trust, cloud-native security, compliance mandates, and data governance. They must also anticipate new threat vectors, such as supply chain attacks, IoT vulnerabilities, and API abuse, while designing architectures that are resilient, scalable, and cost-effective.
A Multifaceted Skill Set
A modern cybersecurity architect must possess a wide array of skills, including:
- Threat modeling and risk assessment: Identifying potential attack paths and prioritizing threats based on risk.
- Secure enterprise architecture: Designing networks, applications, and cloud systems that are secure by design.
- Cryptographic standards: Knowing when and how to apply encryption, hashing, and secure key management.
- Compliance and governance: Ensuring systems comply with frameworks such as NIST, ISO 27001, HIPAA, and GDPR.
- Security operations integration: Collaborating with SOC teams to ensure detection and response mechanisms are built into the architecture.
- Business continuity and disaster recovery: Designing architectures that minimize downtime and data loss during an incident.
What makes this role particularly challenging is the need to balance technical rigor with business acumen. Architects must communicate complex security strategies to non-technical stakeholders and justify security investments in terms of ROI and business impact.
Offensive Knowledge: A Strategic Advantage
Understanding offensive tactics is no longer just for red teamers or penetration testers. For a cybersecurity architect, knowing how attackers think enables proactive defense and strategic foresight. With insight into exploitation techniques, lateral movement, privilege escalation, and social engineering, architects can build systems that are not just reactive, but preemptive.
Certifications like CompTIA PenTest+ are invaluable here. While they are typically geared toward ethical hackers and testers, the skills learned, such as vulnerability scanning, enumeration, and exploitation, translate directly to architectural awareness. Architects with this knowledge can perform internal security reviews, challenge assumptions, and design systems that account for real-world attack patterns.
Strategic Governance and Risk Management
At the other end of the spectrum lies the business-focused side of the architect’s role. This includes understanding compliance obligations, third-party risks, internal security policies, and how to communicate security posture to senior executives and board members.
The CISSP certification, provided by (ISC)², is regarded as the gold standard for this level of strategic thinking. CISSP equips professionals with the knowledge to design, implement, and manage comprehensive security programs. It delves deep into domains such as:
- Security and Risk Management
- Security Architecture and Engineering
- Asset Security
- Security Assessment and Testing
- Identity and Access Management
- Software Development Security
By covering both technical and managerial perspectives, CISSP helps architects become well-rounded leaders capable of influencing enterprise-wide decisions.
Bridging the Gap: Tactical and Strategic Mastery
Together, certifications like PenTest+ and CISSP provide the dual lens that modern cybersecurity architects need: a tactical understanding of threats and a strategic approach to governance and business alignment. This combination allows architects to work effectively with hands-on teams while also engaging confidently with legal, compliance, and executive stakeholders.
In an age where cyber threats impact every part of the business, cybersecurity architects must evolve into translators, strategists, and defenders, and these certifications are instrumental in helping them do just that.
3. CompTIA PenTest+: Learn the Attacker’s Mindset
If Security+ teaches you defense, CompTIA PenTest+ teaches you to think like an adversary. This intermediate-level certification validates a professional’s ability to simulate cyberattacks against IT systems and networks, using both automated tools and manual techniques.
Understanding penetration testing helps cybersecurity architects assess risk, design layered security architectures, and anticipate attack vectors. Architects who grasp how attacks evolve can implement systems that don’t just detect threats, they prevent them.
PenTest+ Overview
- Exam Code: PT0-002
- Exam Length: 165 minutes
- Question Types: Multiple choice and performance-based
- Recommended Experience: 3–4 years in security or networking roles
- Cost: Approximately $392 USD
Domains Covered
- Planning and Scoping (14%)
Covers legal compliance, permissions, rules of engagement, and threat intelligence. - Information Gathering and Vulnerability Identification (22%)
Teaches enumeration techniques, network scanning, and OSINT strategies. - Attacks and Exploits (30%)
Tests your ability to exploit web applications, cloud environments, and local devices. - Reporting and Communication (18%)
Emphasizes documentation, stakeholder communication, and strategic recommendations. - Tools and Code Analysis (16%)
Evaluates proficiency with Kali Linux, Nmap, Burp Suite, Metasploit, Python, and PowerShell.
Why Architects Should Care
Penetration testing isn’t just for red teamers. Architects must know how attackers break in so they can design systems that stand up to stress. By earning PenTest+, you gain the ability to:
- Identify architectural weaknesses before implementation
- Design systems with assumed breach and zero-trust principles
- Understand how different attack surfaces interact (cloud, IoT, on-prem)
- Provide more effective guidance to SOC analysts and security testers
How to Prepare
Preparation for PenTest+ involves more than just reading theory. You’ll need hands-on practice, lab simulations, and scenario-based questions. Many professionals use Exam-Labs to test their readiness with real exam simulations and drills that reflect real-world penetration testing environments.
4. CISSP – Certified Information Systems Security Professional
The CISSP, administered by (ISC)², is often referred to as the “MBA of cybersecurity.” Unlike certifications that focus on tools or platforms, CISSP is framework-based and emphasizes policy, governance, and architecture at scale. It’s ideal for those aiming to lead security programs, advise on enterprise-wide security, or step into executive roles.
While the exam is difficult, the payoff is significant. CISSP holders are some of the highest-paid professionals in cybersecurity and are frequently tapped for director, architect, and CISO-level roles.
CISSP Overview
- Administered By: ISC²
- Exam Format: CAT (Computerized Adaptive Testing) in many regions
- Questions: 100–150 questions
- Time Limit: 3 hours
- Experience Required: 5 years of full-time work across 2 of 8 domains
- Endorsement: Must be endorsed by another ISC²-certified professional
Domains Covered
- Security and Risk Management
- Asset Security
- Security Architecture and Engineering
- Communication and Network Security
- Identity and Access Management (IAM)
- Security Assessment and Testing
- Security Operations
- Software Development Security
Each domain includes both technical and managerial content, from cryptography to ethics to vendor risk management.
Why CISSP Matters for Architects
CISSP isn’t a hands-on certification, it’s a strategic one. It shows that you can:
- Design and validate enterprise security programs
- Align architecture to business risk, legal obligations, and compliance needs
- Manage vendor relationships and software security lifecycles
- Lead teams and influence policy at the executive level
While PenTest+ is tactical, CISSP is strategic. Holding both gives cybersecurity architects 360-degree credibility in technical and executive conversations alike.
Study Tips for CISSP
The CISSP exam is notoriously tough. The best study plans include:
- Reading the Official ISC² CISSP Study Guide
- Practicing regularly on Exam-Labs, which offers accurate simulations
- Engaging with peer groups, Discord study servers, and ISC² forums
- Memorizing frameworks such as NIST SP 800-53, COBIT, and ISO 27001
CISSP is not just about memorizing answers, it’s about learning how to think like a decision-maker, not just a technician.
Combining PenTest+ and CISSP: Tactical and Strategic Mastery
By earning both PenTest+ and CISSP, cybersecurity architects demonstrate their ability to:
- Conduct and interpret penetration tests to discover architectural flaws
- Build and manage secure, compliant infrastructure at scale
- Bridge the gap between technical implementation and executive governance
- Work with SOCs, red/blue teams, and leadership to create unified security strategies
This combination is particularly valuable for those aspiring to titles like:
- Cybersecurity Architect
- Information Security Manager
- Enterprise Security Strategist
- Red Team Architect
- CISO in Training
Real-World Use Cases
Here’s how PenTest+ and CISSP knowledge would be applied in real-world situations:
- Scenario 1: A cybersecurity architect needs to redesign a financial app’s backend infrastructure. With PenTest+ skills, they can simulate potential attacks against the API and databases. With CISSP, they can ensure the design aligns with PCI DSS and SOX compliance standards.
- Scenario 2: A company migrates to Azure. The architect, using knowledge from PenTest+, helps design tests for Azure AD security misconfigurations. With CISSP, they present a governance plan to executive leadership, ensuring long-term operational security.
- Scenario 3: During a post-incident analysis, the architect uses PenTest+ methodology to retrace the attacker’s steps, while applying CISSP frameworks to rebuild trust and ensure future resilience through business continuity planning.
Mastering Offensive Security with the Certified Ethical Hacker (CEH)”
As the cybersecurity threat landscape continues to evolve, security architects need more than just a solid understanding of frameworks and network design, they must also grasp the tools and tactics used by cyber attackers. Being able to anticipate malicious behavior, reverse-engineer attack vectors, and build infrastructures resistant to breaches are crucial skills for today’s security leaders.
In this series, we explored foundational credentials like Microsoft SC-100 and CompTIA Security+. Part 2 took us deeper with PenTest+ and CISSP, bridging the tactical and strategic domains of cybersecurity. We spotlight the Certified Ethical Hacker (CEH) certification – an essential badge of knowledge for cybersecurity architects who want to design systems with an attacker’s mindset.
Offensive Security and the Role of the Cybersecurity Architect
Offensive security is no longer limited to red teams and penetration testers. Architects must understand how cyberattacks unfold across all layers: application, network, infrastructure, and endpoint. They must assess how systems behave under stress, where gaps in detection exist, and how to build resilient structures that can withstand even sophisticated, multi-stage attacks.
This is where CEH proves its value. It’s not just a technical certification; it’s an immersive experience into the world of ethical hacking. It arms professionals with deep insight into how attackers think, plan, and execute. As a result, security architects can anticipate threats during the design phase, reducing costly redesigns and future incidents.
5. Certified Ethical Hacker (CEH)
Administered by EC-Council, the Certified Ethical Hacker is one of the most globally recognized certifications in the field of offensive cybersecurity. It’s designed to equip professionals with the knowledge of hacking tools, techniques, and countermeasures, and trains them to act like adversaries to better defend systems.
CEH Overview
- Certification Body: EC-Council
- Exam Code: 312-50 (ANSI version)
- Exam Format: 125 multiple-choice questions
- Time Limit: 4 hours
- Experience Recommended: 2 years in IT security
- Prerequisites: None, but official training is strongly recommended for exam eligibility
- CEH Practical Exam: Optional hands-on practical exam (6-hour lab test)
CEH Domains
The CEH exam is structured into the following domains:
- Information Security and Ethical Hacking Overview
Concepts of attack vectors, hacker categories, and legal considerations. - Reconnaissance Techniques
Passive and active reconnaissance, footprinting, and open-source intelligence (OSINT). - System Hacking Phases and Attack Techniques
Privilege escalation, maintaining access, covering tracks. - Network and Perimeter Hacking
ARP poisoning, DNS spoofing, man-in-the-middle (MITM) attacks, and evasion techniques. - Web Application Hacking
SQL injection, XSS, CSRF, and other OWASP Top 10 vulnerabilities. - Wireless Network Hacking
Exploiting Wi-Fi protocols and bypassing encryption schemes. - Mobile Platform, IoT, and OT Hacking
Targeting Android, iOS, connected devices, and SCADA environments. - Cloud Computing
Enumerating cloud infrastructure, exploiting misconfigurations, abusing API keys. - Cryptography
Understanding encryption, hashing, cracking algorithms, and cryptographic attacks.
Why CEH Is Valuable for Cybersecurity Architects
While CEH is commonly associated with red teamers and penetration testers, it offers exceptional value for security architects. Here’s why:
1. Designing with Attack Vectors in Mind
Architects equipped with CEH-level knowledge understand how attacks unfold and which entry points are most vulnerable. They can design systems that reduce attack surfaces, apply microsegmentation, and implement deception technologies.
2. Bridging Blue and Red Team Operations
Architects often work with both defenders (blue teams) and ethical hackers (red teams). With CEH training, you can serve as the translator between detection and exploitation, ensuring that both sides operate with architectural awareness.
3. Strengthening Pre-Deployment Reviews
Before rolling out a new application or system, architects must evaluate its security posture. CEH knowledge helps you ask the right questions, run pre-deployment tests, and spot issues early—saving organizations time and money.
4. Staying Ahead of the Curve
CEH emphasizes tools and tactics that reflect modern attack strategies, such as abusing SaaS platforms, targeting APIs, exploiting cloud misconfigurations, and chaining multiple exploits across vectors. This helps architects design with forward-thinking resilience.
CEH vs. PenTest+: Which Should You Choose?
You might wonder whether to pursue PenTest+ or CEH, or both. While there is overlap, the certifications differ in intent and style:
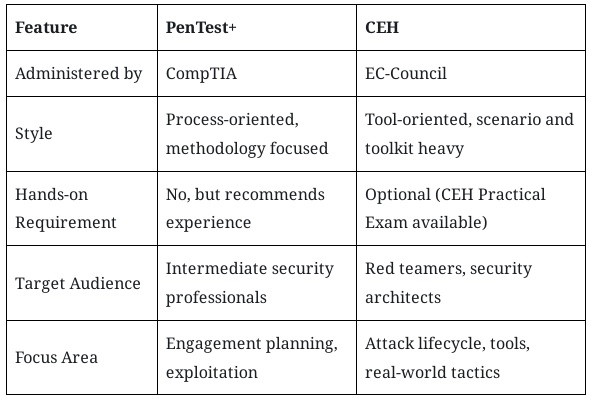
For architects, having both is ideal. PenTest+ helps structure how you think through a testing engagement; CEH adds real-world tooling and attack scenarios. Together, they give you full visibility from reconnaissance to remediation.
Preparing for CEH
The CEH exam requires understanding hundreds of tools and scenarios. Preparation must be structured and immersive. Here’s a recommended approach:
1. Use Official EC-Council Materials
Start with the CEH V12 eCourseware. It offers slide decks, labs, and knowledge checks for each domain.
2. Practice in Labs
Hands-on practice is essential. You should become comfortable with tools such as:
- Nmap
- Wireshark
- Burp Suite
- Metasploit
- Hydra
- John the Ripper
- Aircrack-ng
- OWASP ZAP
Use platforms like Exam-Labs to simulate CEH exam questions and labs. They offer domain-focused quizzes, mock tests, and a test engine that mimics the actual certification environment.
3. Join Ethical Hacking Communities
Get involved in online communities like:
- Reddit’s r/ethicalhacking
- Discord servers dedicated to CEH prep
- LinkedIn CEH study groups
Here you can share strategies, clarify topics, and exchange notes with other learners.
Real-World Applications of CEH Knowledge
To understand how CEH benefits an architect, consider these practical scenarios:
Scenario 1: Cloud Deployment Planning
You’re tasked with designing a multi-cloud solution. With CEH insights, you spot insecure API usage and token storage issues during planning. You add IAM policies and detection mechanisms before the system goes live.
Scenario 2: Vendor Selection
A SaaS vendor claims their platform is secure. With CEH skills, you evaluate their environment for weak encryption practices and suggest improvements in their API access controls.
Scenario 3: Red Team Collaboration
Your company runs quarterly penetration tests. You work directly with the red team, helping them understand system logic while gathering critical feedback for architecture adjustments.
In each of these situations, your ability to think like an attacker informs better design decisions.
CEH and the Cybersecurity Architect’s Career Path
Holding the CEH places you in a strong position for roles such as:
- Cybersecurity Architect
- Red Team Architect
- Security Solutions Designer
- Offensive Security Strategist
- Vulnerability Management Lead
Combined with SC-100, PenTest+, or CISSP, CEH adds technical depth to your résumé, showing that you not only build systems, but you build them to be unbreakable.
Building a Long-Term Cybersecurity Certification Strategy
As we conclude our series on essential certifications for cybersecurity architects, it’s time to look at the big picture, how each certification fits into a structured career strategy and how professionals can build a long-term roadmap toward becoming expert-level security architects, consultants, and even CISOs.
In Part 1, we introduced foundational certifications like Microsoft SC-100 and CompTIA Security+ to help build a strong security base. Part 2 took a step further with CompTIA PenTest+ and CISSP, offering a blend of tactical and strategic skills. In Part 3, we examined the Certified Ethical Hacker (CEH), highlighting its value in teaching cybersecurity professionals how to think like adversaries.
Now, in Part 4, we’ll show how to sequence these certifications, integrate your knowledge, and create a sustainable career development path in the fast-evolving cybersecurity landscape.
Why Certification Strategy Matters
Cybersecurity architects are expected to know more than just firewalls and passwords. They’re expected to:
- Build scalable, secure, and compliant infrastructure
- Understand legal and regulatory requirements
- Collaborate with stakeholders across IT, DevOps, and business teams
- Stay updated on new threats, vulnerabilities, and tools
- Lead security initiatives from conception to implementation
With such a vast range of responsibilities, no single certification will cover it all. That’s why building a certification stack that evolves with your role and goals is critical.
The five certifications we’ve covered throughout this series provide that structured progression, each one serving a purpose, building off the last, and contributing to a well-rounded professional profile.
A Recap of the Five Certifications
Before we dive into sequencing and strategic planning, let’s briefly revisit the five certifications we’ve covered:
- Microsoft Certified: Cybersecurity Architect Expert (SC-100)
Designed for professionals who lead enterprise security design and planning, with emphasis on cloud and hybrid infrastructure. - CompTIA Security+
A foundational certification that introduces key concepts in access control, risk management, and secure networking. - CompTIA PenTest+
Focused on ethical hacking, vulnerability assessment, and penetration testing methodologies. - CISSP – Certified Information Systems Security Professional
The industry standard for cybersecurity leaders, emphasizing governance, architecture, and risk management. - CEH – Certified Ethical Hacker
A technical certification offering deep insights into attacker tools, methodologies, and countermeasures.
Certification Sequencing for Career Growth
How should you structure your certification journey? Here’s a recommended sequence, broken down into career phases:
Phase 1: Getting Started (0–2 Years Experience)
- Start With: CompTIA Security+
Ideal for entry-level professionals or IT generalists making the transition into cybersecurity. This certification provides the vocabulary, threat models, and core principles every security expert must understand. - Then Add: Microsoft SC-100
While more advanced, SC-100 is ideal for those in hybrid cloud environments or existing IT pros looking to specialize in cloud security design. You don’t need years of experience to begin SC-100 prep if you’re already using Microsoft Azure or M365 environments.
Phase 2: Mid-Level Development (2–5 Years Experience)
- Add: CompTIA PenTest+
As you become more comfortable with cybersecurity fundamentals, PenTest+ introduces offensive tactics and ethical hacking methodology. Even if you don’t plan on becoming a red teamer, this insight is essential for designing hardened systems. - Supplement With Hands-On Practice
Use simulation platforms like Exam-Labs to gain exposure to real-world scenarios. These hands-on environments are crucial for mastering exam material and translating it into job performance.
Phase 3: Strategic Advancement (5–10 Years Experience)
- Earn: CISSP
By now, you’ll be ready to tackle management-level topics such as security governance, compliance frameworks, and architecture at scale. CISSP is the gold standard in cybersecurity and often a requirement for senior leadership roles. - Understand: Risk, Legal, and Compliance Strategies
CISSP opens the door to security leadership and executive decision-making, which requires you to manage not just technology, but also business risk.
Phase 4: Offensive Mastery and Specialization (5+ Years Experience)
- Add: CEH – Certified Ethical Hacker
Even in a senior security architect role, understanding the nuances of attack tools and red team tactics will help you collaborate with security testers and build defensible architectures. CEH’s real-world tooling focus sets it apart from PenTest+’s methodology-heavy approach.
Building a Well-Rounded Cybersecurity Portfolio
By combining all five certifications, you position yourself as a cross-functional cybersecurity expert. Here’s how your knowledge areas will look:
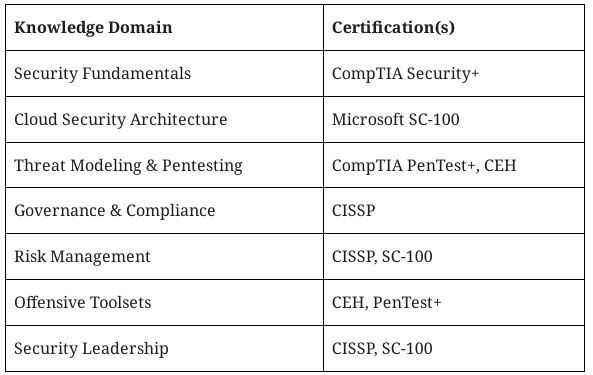
This combination of skills ensures you’re equipped to:
- Lead architecture design for secure hybrid environments
- Anticipate and mitigate attacks with an adversarial mindset
- Maintain compliance with regulations like GDPR, HIPAA, and PCI-DSS
- Work across technical and executive teams
- Drive long-term security strategies
Salary Expectations and Role Evolution
Professionals holding these certifications can expect substantial compensation growth and increasing responsibilities over time.
Estimated Salaries Based on Certification Stack:
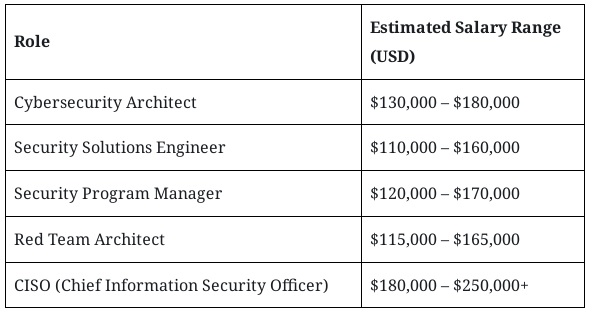
These roles are found across industries including healthcare, banking, energy, SaaS, telecommunications, and government agencies.
Maintaining and Renewing Your Certifications
Most of these certifications require continuing education or renewal every 2–3 years. Here’s how to manage that:
- Use Exam-Labs for Continued Learning
Stay current by engaging with updated quizzes, mock exams, and scenario reviews. Even if you’ve passed the exams, this platform helps maintain your edge. - Earn CPEs (Continuing Professional Education credits)
Attend webinars, write articles, contribute to open-source security projects, or mentor junior professionals. These activities often count toward renewal. - Cross-Train into Emerging Domains
Consider specialized certifications in areas like cloud security (CCSP), incident response (GCIH), or DevSecOps depending on your focus area.
Final Thoughts: The Architect’s Role is Strategic
The world needs more cybersecurity professionals who can think deeply and act strategically. A well-rounded cybersecurity architect isn’t just someone who knows how to deploy firewalls or block IP addresses. Instead, they are security designers, risk managers, and strategic advisors capable of safeguarding organizations at every level.
By earning the five certifications we’ve explored in this series, SC-100, Security+, PenTest+, CISSP, and CEH, you are developing not just your technical expertise, but also your credibility, influence, and leadership ability.
Next Steps: If you’re early in your journey, begin with Security+ or SC-100. For those already mid-career, adding PenTest+ and CISSP can significantly elevate your trajectory. Top off your certification stack with CEH to deepen your offensive skillset and bring full-circle awareness to your security strategy.
Use resources like Exam-Labs to prepare efficiently, stay current with evolving exam objectives, and test your knowledge in realistic environments. Building a strong cybersecurity career is a marathon, not a sprint, but with the right tools and certifications, you’ll be miles ahead of the curve.
